
A Guide on Mitigating Cloud Adoption Risks Based on MAS’ Advisory
by Fintech News Singapore September 7, 2021Although organisations across many sectors have accelerated the adoption of cloud environments, the financial institutions (FIs) have been rather reluctant in migrating their services to the cloud.
Core transaction processing and other mission-critical tasks are still running on legacy on-premises systems.
However, the changes brought by the pandemic to business models and customer interaction have become an enabler for faster adoption of public cloud platforms by banks and other financial institutions.
The Monetary Authority of Singapore (MAS) had previously issued an advisory highlighting some key risks and control measures that FIs should consider before adopting public cloud services in June 2021.
While the advisory does not set out legal obligations per se, MAS does offer specific guidance on managing cloud-related risks.
Thales reviewed MAS’ advisory on addressing the technology and cyber security risks associated with public cloud adoption in an e-book.
Weighing the benefits and risks of cloud adoption
- The pros and cons of the cloud aren’t unique to banks.
- Better agility, scalability, and elasticity.
- Ability for financial companies to deploy more efficient processes or data-intensive applications.
- Quicker transaction processing times for the consumer or faster and more tailored customer service options.
Despite the benefits, the cloud introduces cybersecurity risks that weren’t present in legacy systems. For example, the advisory notes that many public cloud security incidents, such as data leaks, were caused by poor management on the user’s end (e.g., poor control of access to the service provider’s cloud).
The security of the cloud versus more traditional infrastructure like on-premises data centers is more complex and requires financial institutions to act proactively and have a design-by-security mentality.
Monetary Authority of Singapore offers cloud security advisory
In response to these challenges, the Monetary Authority of Singapore (MAS) has issued an advisory to provide the financial institutions in Singapore with sound advice on managing and mitigating the cybersecurity risks of public cloud adoption.
The advisory highlights the following areas of consideration for the financial institutions:
- Perform a comprehensive risk assessment as they plan for public cloud adoption and manage the risks identified appropriately.
- Develop a public cloud risk management strategy that takes into consideration the unique characteristics of public cloud services.
- Implement strong cybersecurity controls in areas such as Identity and Access Management (IAM), data protection and cryptographic key management.
- Ensure staff have adequate skillset to manage public cloud workloads and risks.
FIs need to double down on identity and access management
Identity and Access Management (IAM) is the cornerstone of effective cloud security risk management.
The MAS Cloud Advisory notes in Item 10 that financial institutions should enforce the principle of “least privilege” stringently when granting access to information assets in the public cloud.
The IAM strategy should focus on the following:
- Implement multi-factor authentication (MFA) (Item 11).
- Regularly change the credentials for authentication in the public cloud, such as “access keys” (Item 12).
- Centrally manage IAM policies for accessing multiple public cloud services and ensure that the policies are consistently enforced (Item 14).
Data security measures needs to be ramped up
Item 21 of the MAS Cloud Advisory requires financial institutions to implement appropriate data security measures to protect the confidentiality and integrity of sensitive data in the public cloud, taking into consideration data-at-rest, data-in-motion where applicable.
- For data-at-rest, financial institutions should tokenization in addition to the encryption provided at the platform level.
- For data-in-motion, financial organizations are advised to implement session encryption in addition to the encryption provided at the platform level.
In addition to the protection offered by data encryption, financial institutions should adopt cryptographic key management strategies to enable a robust and consistent level of control and protection of their cryptographic keys and to avoid the compromise of these keys.
The advisory suggests two options:
- Bring Your Own Key (BYOK) to retain control and management of cryptographic keys that would be uploaded to the cloud to perform data encryption.
- Bring Your Own Encryption (BYOE) where data is encrypted before it enters the cloud, and the keys are not transferred to the cloud.
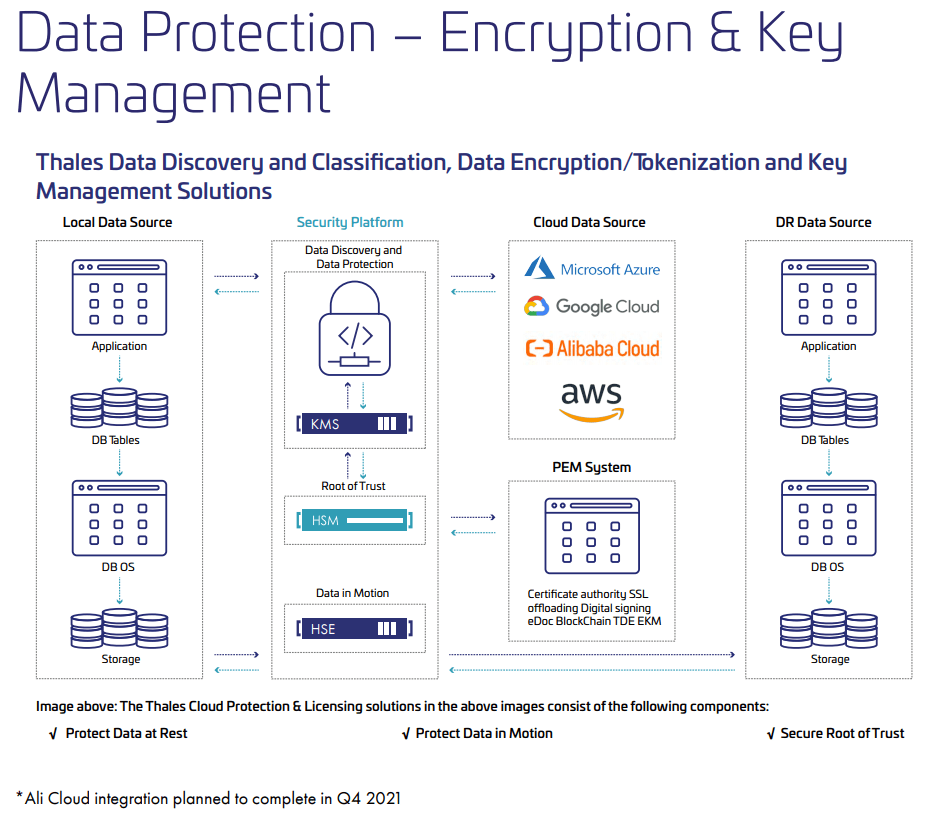
Source: A Review of the Monetary Authority of Singapore (MAS) Advisory on Addressing the Technology and Cyber Security Risks Associated with Public Cloud Adoption e-book
Avoid vendor lock-in risks
To ensure a strong cloud security posture, banks and financial institutions should establish and enforce robust cloud security controls.
While cloud service providers offer native security solutions, the advisory notes in Item 34 that “[financial institutions] should establish a process to assess their exposure to [cloud service providers] lock-in and concentration risk.”
The shared responsibility model of cloud security gives institutions the freedom to choose the security controls of their preference which integrate with their infrastructure and address their business needs in the most effective manner.
Opting for a neutral cloud security solution presents many advantages to financial institutions, such as controlling your own regulatory compliance regime and your own cloud security posture.
How Thales helps
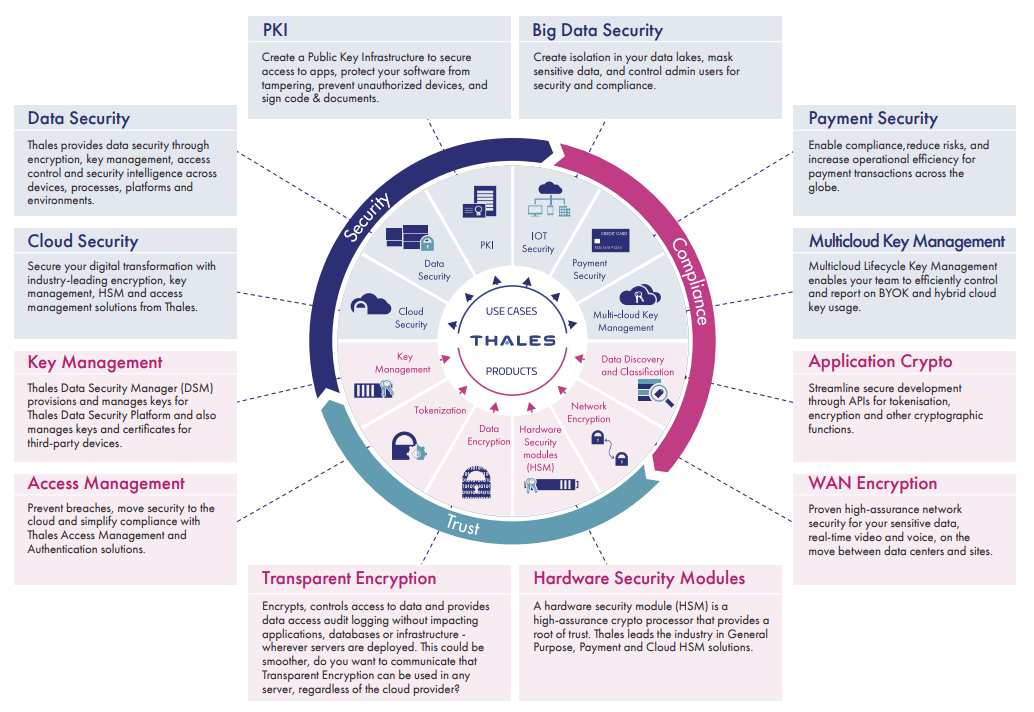
Managing the cloud security risks requires tailor-made solutions. Thales’s industry-leading products enable enterprises to centrally manage and secure access to applications, and to protect and remain in control of their data — both on and off the cloud.
- SafeNet Trusted Access, Thales’s cloud-based access management and authentication service, supports numerous authentication methods and allows you to leverage authentication schemes already deployed in your organization.
- CipherTrust Transparent Encryption (CTE) offers file system encryption for cloud instance or premises servers with external key management.
- High Speed Network Encryption (HSE) solutions protect any kind of data moving from on premises infrastructure to the cloud.
- CipherTrust Cloud Key Manager (CCKM) enables organizations to implement BYOK policies and retain control and management of cryptographic keys uploaded to the cloud to perform data encryption.
- CipherTrust Transparent Encryption (CTE) is a BYOE solution that provides encryption to the files before being transferred to cloud storage.
Download Thales’ e-book reviewing MAS’ advisory on addressing the technology and cyber security risks associated with public cloud adoption here.
Featured image credit: Technology photo created by rawpixel.com – www.freepik.com





